How to Keep Passwords Safe (Ultimate Guide & Easy Steps)

Imagine waking up one day and finding your bank account empty. Or seeing your social media hijacked.
For too many people, this nightmare isn’t hypothetical, it’s reality. And most of the time it all starts with something as small and invisible as a weak or stolen password.
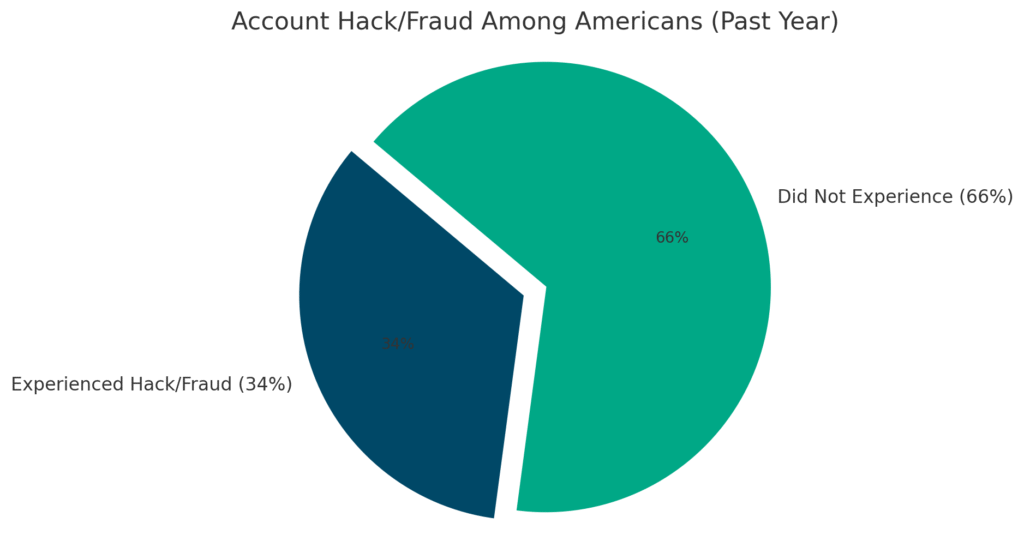
In fact, nearly 34% of Americans experienced some form of account hack or fraud in just the past year (PewResearch.org).
Hackers don’t care who you are. They go after everyone, teenagers, seniors, even major corporations.
Remember when a single compromised password helped shut down a U.S. fuel pipeline, sparking gas shortages? (TheHackerNews.com) That’s the world we live in.
The stakes are high, and emotional. When you lose money, privacy, or trust in your digital life, it cuts deep.
That’s why this guide exists. We’re going to show you exactly how to protect yourself.
Not theory, real examples and proven tips.And yes, we’ll sprinkle in some stats along the way to keep it real.

If you’ve ever felt anxious about password security, you’re definitely not alone. Roughly seven in ten Americans say they feel overwhelmed by how many passwords they have to juggle. And nearly half worry their passwords aren’t secure enough (PewResearch.org).
But here’s the good news:
By the time you finish this guide, you won’t feel stuck or anxious anymore. We’ll cover it all, from how to create bulletproof passwords to why a password manager isn’t optional anymore.
By the end, you’ll have the confidence (and the tools) to lock down your accounts for good. Let’s dive in.
Why Password Safety Matters (Yes, It’s a Big Deal)

Your passwords are the keys to your kingdom. And really, would you put a cheap lock on your front door?
Of course not.
So why would anyone treat their digital life differently? Yet millions do — and that’s exactly what cybercriminals count on: easy targets.
Here are a few eye-opening reasons why password safety is critical:
Data Breaches Are Booming:
Huge leaks happen all the time — exposing millions of passwords. In 2023 alone, over a third of Americans had at least one online account breached by hackers (PewResearch.org).
If you reuse passwords (and let’s face it, many people do), one breach can lead attackers straight into your other accounts.
It’s like a domino effect of disaster.
Real-Life Horror Stories:
Consider Lisa’s story — a graphic designer who used the password “lisa2020” across several sites.
Hackers easily cracked it and took over her life:
they drained her bank funds, spammed her friends from her email, even leaked personal photos (elm.umaryland.edu).
All that damage stemmed from one weak, reused password. It can happen to anyone — and the fallout is painful.
Shocking Statistics:
According to the Verizon Data Breach report, a staggering 81% of hacking-related breaches involve lost or weak passwords (bnd.nd.gov).
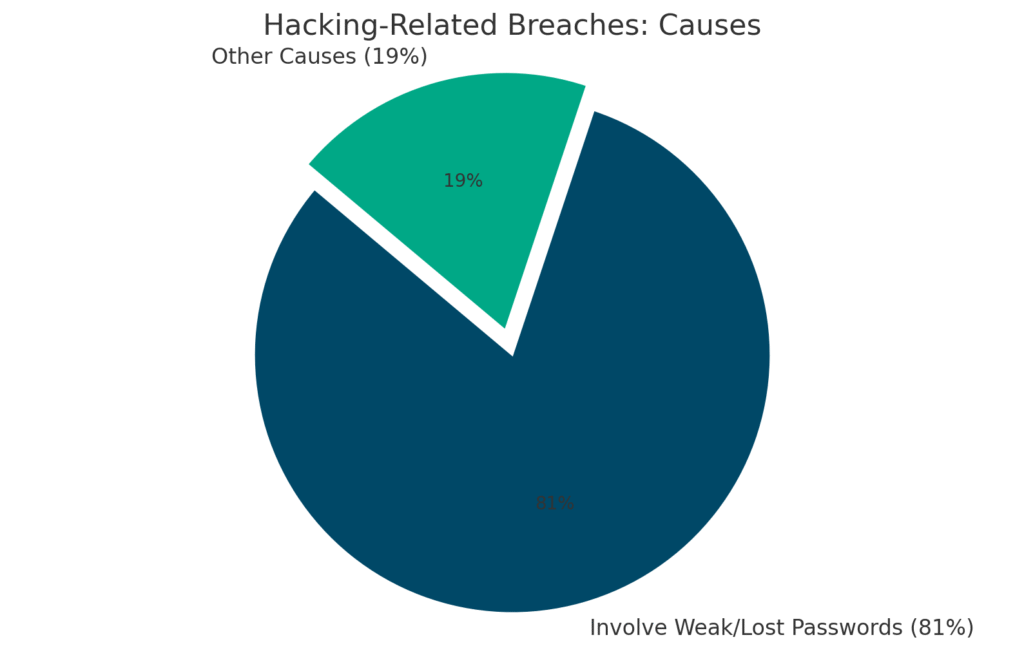
Think about that — the vast majority of hacks could be stopped by stronger, better-protected passwords!
Also, about 64% of Americans have personally experienced some form of data theft like fraudulent charges or account takeovers (PewResearch.org).
Weak passwords are often the culprit behind these incidents.
Financial & Emotional Costs:
When passwords get compromised, it’s not just an “IT problem.” It can cost real money and heartache.
Identity thieves can open credit lines in your name. Ransomware attackers can lock your files. Scammers can impersonate you.
In 2021, a single stolen password led to a multi-million dollar ransomware attack on Colonial Pipeline, causing fuel shortages and panic buying (TheHackerNews.com).
For an individual, the loss might be a drained savings account or stolen IRS refund — devastating consequences nobody wants to face.
Bottom line:
Password safety matters because your entire digital life — finances, personal communications, business data — rests on those little strings of characters.
The good news?
With a few smart habits, you can slam the door in hackers’ faces and sleep easier.
Let’s explore the best ways to do that.
The Best Ways to Keep Your Passwords Safe (Actionable Tips)
Now we get to the heart of it: how you can keep your passwords (and accounts) safe starting today.
We’re going to cover proven, practical steps. And don’t worry — none of this is rocket science. Even if you’re not “tech-savvy,” you can do these!
Let’s break it down:
Use Strong, Unique Passwords for Every Account
If you do nothing else, do this: make sure each of your accounts has a strong (hard-to-guess) and unique (not reused anywhere) password.
It’s the single most important step to prevent the domino effect of one hacked account leading to many.
Go Long – Use Passphrases:
The longer your password, the tougher it is to crack. Experts recommend at least 12–15 characters (consumer.ftc.gov).
A great approach is using a passphrase — a few random words strung together.
For example: sunflower_movie_!guitar is far stronger (and easier to remember) than a short jumble of random characters.
In fact, the UK’s cyber security agency suggests the “three random words” rule, combining three unrelated words for a strong password (ncsc.gov.uk).
Just avoid common phrases or quotes — make it unique to you (consumer.ftc.gov).
Mix It Up:
If you’re creating your own password, include a mix of uppercase and lowercase letters, numbers, and symbols for extra strength (consumer.ftc.gov).
For example: add punctuation or a number somewhere in your passphrase. That said, length matters more than weird characters. HoneybeesCoffeeRed! is incredibly strong just because of its length, even though it’s mostly words with a single symbol.
Hackers’ password-cracking tools struggle far more with a 16-character passphrase than an 8-character “complex” word.
No Personal Info:
Don’t use your name, birthdate, kids’ names, or any other personal details in passwords. Hackers can guess or find that info easily.
Also avoid super-common passwords like password, 123456, or keyboard patterns like qwerty — those are literally the first things attackers try. (Fun fact: “123456” still tops the worst password list every year — and gets hacked in milliseconds.)
Never Reuse Passwords:
Reusing a password on multiple sites is like using one key for your house, car, and office. If that key gets stolen, everything is at risk.
Unfortunately, 59% of people admit to reusing passwords even though they know it’s dangerous (bnd.nd.gov). Don’t be part of that stat.
If a breach at one site exposes your login credentials, criminals will immediately try those same details elsewhere, a tactic called credential stuffing (enzoic.com).
For example, when millions of LinkedIn passwords leaked a few years ago, hackers quickly used them to break into Gmail, Facebook… you name it.
One site’s breach should never jeopardize your other accounts.
Pro Tip:
Having trouble coming up with a strong password? Let a computer do it for you! Many services and browsers can auto-generate secure passwords (consumer.ftc.gov).These often look like random strings — Xj#9Lp!z&… — impossible to remember… but that’s fine, because we’ll manage them easily in the next step.
Get a Password Manager – Your Personal Vault
Managing dozens (or even hundreds) of unique, complex passwords might sound impossible — and that’s exactly where password managers come to the rescue.
A password manager is a secure app that stores all your passwords so you only have to remember one master password.
It’s basically a vault for your digital keys, protected by heavy encryption and your master key.
How Password Managers Help:
They generate ultra-strong passwords for you, store them encrypted, and auto-fill them when you log in. No more memory gymnastics or sticky notes.
With a manager, you can have a 20-character gibberish password for every account and still log in with a click. This directly solves the reuse problem — and the all-too-human tendency to pick easy passwords (enzoic.com).
In fact, a recent survey found that 70% of Americans feel overwhelmed by passwords (PewResearch.org). A manager takes that burden off your shoulders.
Security Benefits:
A good password manager uses zero-knowledge encryption — meaning even the company itself can’t read your passwords. Only you can, with your master password (Comparitech.com).
Your vault is typically encrypted with industry-strength algorithms like AES-256 (Comparitech.com). Many managers will also alert you if any of your passwords show up in a known breach, so you can change them ASAP.
And here’s the kicker: leading password managers have never been hacked or had their vault data stolen (Comparitech.com). Contrast that with not using one — if your browser or notebook is compromised, all your passwords could be exposed.
Choosing a Reputable Manager:
Stick with well-known, trusted brands — we’ll compare a few top options in the table below. Look for features like cross-platform support (so it works on both your phone and computer), ease of use, and two-factor authentication on the vault itself for extra safety.
It’s worth noting that no tool is 100% immune.
For example, LastPass (a popular manager) had a serious breach in 2022 that shook user trust. But other top services like Bitwarden, 1Password, and Dashlane have never had their encrypted vaults compromised (Comparitech.com).
They’ve undergone third-party security audits and built strong reputations. Do a bit of research and pick one that fits your needs — many offer free versions or trials.
One Master Password to Rule Them:
When you use a manager, you’ll create a single master password. Make that one very strong — it’s the key to your entire vault. Use a long passphrase that you won’t forget but no one else could guess.
And enable two-factor authentication on the manager itself if available. That way, even if someone somehow got your master password, they’d still need a second factor to unlock your vault.
- Convenience Factor:
Once you’re set up, your password manager will auto-fill logins for you on websites and apps — super convenient, especially on your phone. Many can even store other info like credit cards or secure notes. - The first time you try it, you’ll feel like you discovered a life hack. No more password reset emails. No more scribbled notes. It’s a productivity boost and a security boost — all in one.
Which password manager is the safest and has never been hacked?
While no security product can promise it will never be hacked, several top managers have clean slates — no history of breaches.
For example, Dashlane, Bitwarden, 1Password (and newer tools like RelyPass) have never been compromised or leaked customer vaults (Comparitech.com). These companies use strong encryption and undergo regular security audits.
The key is to pick a reputable manager — and protect your master password carefully. (And yes, LastPass is technically “safe” to use now… but its 2022 incident showed why a zero-knowledge policy and user-controlled encryption really matter.
After that breach, many users switched managers — and that’s worth keeping in mind.)
Turn On Two-Factor Authentication (2FA) – Double Up Your Security
Even the strongest password can be stolen. That’s why two-factor authentication is a must wherever it’s available.
2FA (also called two-step verification) simply means you need two things to log in:
something you know (your password) and something you have (like a code on your phone or a physical key).
It’s like needing a second key in addition to your password.
Why 2FA is Vital:
If someone guesses or steals your password, they still can’t get into your account if 2FA is turned on — because they won’t have that second factor.
Remember those Colonial Pipeline hackers? They got in because the company’s old VPN only required a password — no 2FA (Reuters.com).
Don’t make that mistake.
Security experts widely agree: 2FA is the single best defense against password theft (Reuters.com). Even if your password gets exposed in a breach or stolen through phishing, 2FA can stop thieves cold.
Common 2FA Methods:
The most common form is a one-time code sent to your phone (via text or an authenticator app) (Consumer.ftc.gov).
You enter that six-digit code after your password to prove it’s really you.
Authenticator apps (like Google Authenticator, Authy, etc.) generate codes that refresh every 30 seconds — these are more secure than SMS texts and free to use.
Some services also support push notifications (where you tap “Yes, it’s me” on your phone) or physical security keys (USB or NFC devices you plug in).
For your most sensitive accounts — email, banking, etc. — consider using an authenticator app or security key rather than SMS codes (Consumer.ftc.gov). They’re safer.
Set It Up Everywhere You Can:
Turn on 2FA for your email, social media, banking, cloud storage — basically any account that offers it. Major platforms like Google, Apple, Facebook, Microsoft, Twitter, Amazon, and more all support 2FA in some form.
Yes, it adds a small extra step at login, but most let you “remember” trusted devices so you won’t have to do it every time. And honestly? The peace of mind is well worth it.
Tip for Beginners:
Start with 2FA on your email account first.
Why? Because your email is the gateway to resetting all your other passwords. If hackers get into your email, they can request password resets everywhere else and take over those accounts too.
So lock down your email with 2FA first — then add it to your other key accounts.
Beware of Phishing – Don’t Take the Bait

Not all password theft happens by brute force.
Phishing is a huge threat — that’s when scammers trick you into giving up your password by pretending to be a legitimate site or person.
They might send a fake email that looks like your bank… or a text that seems to be from a friend, but with a suspicious link.
If you click and enter your login details on that bogus site? You just handed your credentials to criminals.
How to Spot Phishing:
Be skeptical of emails or messages asking for your password or personal info,
or trying to get you to click a login link. Always check the sender’s address —
is it truly from the company’s domain?
(For example, an email from Microsoft won’t come from micros0ft support@gmail.com — note the subtle misspelling.) Never enter your password via an email link unless you are 100% sure it’s legit.
When in doubt, go directly to the website yourself — type your bank’s URL manually instead of clicking any links.
Phishing messages often try to create urgency or fear: “Your account will be closed unless you log in now!” That’s a classic red flag (elm.umaryland.edu).
Verify, Verify, Verify:
If you get an unexpected alert — like “Your account was compromised, log in here to fix it” — verify through another channel.
Call the company’s official support line or navigate to your account via a trusted app or saved bookmark. Don’t trust scary pop-ups or unsolicited emails. Legit companies never ask you to confirm your password via email.
Don’t Share Codes Either:
With 2FA in place, scammers might try a new trick: pretending to be support and asking for the 2FA code texted to you “to verify your identity.”
Never share your authentication codes or one-time PINs with anyone. No real company will ever ask for that code sent to your phone — it’s for you alone to use. If someone’s asking for it, it’s a scam. Period.
Educate Yourself:
Phishing tactics evolve all the time, so stay informed. Some phishing emails are surprisingly convincing — real logos, professional formatting… they can look legit.
A healthy dose of paranoia online is actually a good thing. Remember Lisa from earlier?
In her case, she clicked a fake bank email and entered her password on a scam site —
and that’s how hackers stole her credentials in the first place (elm.umaryland.edu).
If something feels off about a message? Trust your gut.
Never Store Passwords in Unsafe Places
Keeping a strong password is only half the battle — you also need to store it securely. A password manager, like we talked about earlier, is the best place to do that. But what about all those other places people tend to stash passwords?
Here’s some straight talk on what not to do:
Say NO to Sticky Notes and Notebooks:
It might feel convenient to jot passwords on a sticky note under your keyboard or in a little notebook… but physical notes can easily be lost, stolen, or even spotted by house guests.
(Honestly — how many of us have seen a coworker’s email password stuck to their monitor? It happens.) If you must write passwords down, keep them in a locked drawer or safe — not on your desk or in your wallet.
And definitely don’t label the paper “My Passwords” — that’s basically an open invitation if anyone ever burgles your home.
Don’t Use Plain Text Files or Spreadsheets:
Storing passwords in a Word doc, Notepad file, or Excel sheet on your computer is risky unless the file is encrypted. If your computer gets malware or someone gains access, those files are basically a buffet of your logins.
Especially avoid cloud spreadsheets like Google Sheets for password storage.
They are not designed to be secure vaults.
In fact, Google Sheets are not end-to-end encrypted, which means Google (or anyone who hacks your Google account) could potentially read that data (KeeperSecurity.com).
If your Google account is compromised, a hacker could easily rummage through your Drive and find your password sheet (KeeperSecurity.com).
Plus, it’s easy to accidentally share an online doc with the wrong person —
instantly exposing all your secrets (KeeperSecurity.com).
Bottom line: Google Sheets or Excel files full of passwords = bad idea (KeeperSecurity.com).
Beware of Browser “Save Password” without Protections:
Your browser probably offers to save passwords — and yes, that’s convenient. But know that those saved passwords are typically protected only by your computer login, at best.
If you do use browser-saving, make sure your computer account is password-protected and you’ve enabled encryption like BitLocker (Windows) or FileVault (Mac). Also keep in mind that if your Google account or Firefox account (for syncing) is ever breached, someone could potentially sync and see your saved passwords.
A dedicated password manager or your device’s built-in manager (like Apple iCloud Keychain) often adds extra security — requiring your fingerprint or device PIN to autofill. Use those features if they’re available.
Do Not Email or Text Passwords:
Never send a password in plain text — whether to yourself or anyone else. Emails and texts can be intercepted or exposed if someone gets into those accounts.
If you need to share a password (like with a family member), use a secure sharing feature in your password manager or just say it verbally — never over email. And definitely never respond to an email asking for your password. Legit companies will never ask for it that way.
Public Computers = No:
Avoid logging into sensitive accounts on public computers (think libraries, hotel business centers, etc.). They could have spyware — and you won’t know it.
And absolutely don’t let a public browser “save” your login. If it’s not your device, just assume it’s not safe for passwords.
Regularly Update and Monitor Your Passwords
Passwords shouldn’t be a “set it and forget it” forever. That doesn’t mean you need to change them on a strict schedule — in fact, NIST no longer recommends routine forced changes because it can actually do more harm than good (Gadellnet.com).
But you should update your passwords promptly if there’s ever a risk.
Change Passwords After Breaches:
If a company announces a breach that affects logins, change your password there immediately — and anywhere else you (hopefully don’t!) reuse that password. Using unique passwords limits the damage to just that one account.
Stay aware of breach news — you can use free services like “Have I Been Pwned” to get notified if your email shows up in a known data leak.
Use Built-in Checkup Tools:
Many password managers and even browsers have security checkup features. They’ll flag weak, reused, or compromised passwords. Take a few minutes to review those reports and update anything flagged.
For example: if your manager tells you your old 2015-era email password was exposed in a breach, swap it out for a fresh strong one.
Keep Contact Info Updated:
Make sure your accounts have an up-to-date email and phone number.
Why? So if suspicious activity occurs — like a login from a new device — you actually get the alerts. Also, if you ever get locked out, it’s much easier to recover access when your contact details are current.
Consider a Password Policy for Yourself:
Businesses have password policies — why shouldn’t you?
For example:
“My bank, primary email, and retirement account passwords will each be 20+ characters and unique.”
You could even write down (or just mentally note) a few personal rules: always enable 2FA when it’s offered, never reuse passwords on sensitive accounts, etc.
Having your own mini security routine helps you stay on track.
Now that we’ve covered the core steps, we can look at some of the tools that can help — specifically password managers — and then dive into advice tailored for different groups of people.
Top Password Managers Compared (Pros & Cons)
A password manager is a cornerstone of safer password practices. Below is a quick side-by-side comparison of four great options — three industry leaders (Bitwarden, 1Password, Dashlane) and a newer player (RelyPass).
All of these will dramatically improve your security versus not using a manager at all. The “best” one really depends on your needs and preferences:
|
Password Manager |
Pros |
Cons |
|
Bitwarden (Free & Paid) |
– Open-source and regularly security-audited (transparent code) (bitwarden.com). |
– Interface is functional but less glossy; might feel a bit technical for some beginners. |
|
1Password (Paid) |
– User-friendly design — great for families and teams, with shared vaults. |
– No free tier — subscription only. |
|
Dashlane (Free & Paid) |
– Rich features: password health reports, dark web monitoring, VPN included in Premium (security.org). |
– Free version is limited (one device, 50 passwords max). |
|
RelyPass (Free iOS app) |
– Free on iOS with unlimited passwords — great for budget-conscious Apple users. |
– Apple ecosystem only: no Android or Windows app (not ideal for multi-platform users). |
Note:
No matter which one you choose, the most important “pro” is simple: any of these tools lets you use strong, unique passwords everywhere without the headache.
Features and pricing aside, just using a reputable password manager is a massive upgrade over reuse or risky storage habits.
A lot of people start with a free version — like Bitwarden’s free tier or RelyPass for iOS —
and upgrade or switch later as their needs evolve.
Tailored Tips for Different Users

One size doesn’t always fit all when it comes to security advice. Everyone’s situation is a bit different. In this section, we’ll provide custom tips for three groups who often have special considerations: beginners, seniors, and teams. If you identify with one (or more) of these, pay extra attention here!
For Beginners: “I’m Not Techy – Where Do I Start?”
If you’re relatively new to all this “password safety” talk, the whole thing can feel overwhelming. Don’t worry — you can start small and still get big benefits. Here’s how:
Start with Your Most Important Accounts:
You don’t have to change every single password today. Just focus on the 2–3 accounts that would hurt the most if compromised. Typically, that’s your email, your bank or financial accounts, and maybe your primary social media.
Why email? Because it controls password resets for everything else — it’s the gatekeeper. Make sure these have strong, unique passwords right now.
Use a Password Manager for “Training Wheels”:
If you’ve never used one, try a free password manager like Bitwarden or RelyPass as a test run. You can start small — store just a few less-critical logins to get comfortable.
Once you see how convenient it is, add your other accounts. Most managers even let you import passwords saved in your browser or a CSV file — setup doesn’t have to be hard.
It’s okay if you don’t fully trust it at first. Try it with low-stakes accounts, build confidence, then move your important ones over.
Remember: password managers exist because humans are bad at creating or remembering strong passwords (consumer.ftc.gov). Let the tool do the heavy lifting.
Create a “Formula” (But Don’t Reuse):
Some beginners use a trick: they come up with a pattern for passwords. For example: maybe your base word is Sunshine! and you add a unique suffix per site — Sunshine!FB for Facebook, Sunshine!AMZ for Amazon.
Caution here though: this is better than outright reuse, but if anyone figures out the pattern, they could crack all your accounts. If you use any formula, make sure it’s not obvious and still includes randomness.
Honestly? Using a password manager to generate truly random passwords is much safer. If you do go with a formula to start, plan to transition to fully unique passwords as you get more comfortable.
Write Down Master Info in a Safe Place (Initially):
If you’re worried about forgetting your new passwords or the master password for your manager, it’s okay to write it down temporarily — just store that paper securely.
Example: keep it in a home safe or lockbox. This gives you a backup while you adjust. Over time, you’ll memorize your master password and you can destroy that paper.
The goal is to avoid getting locked out, but also keep that info away from prying eyes. (And no — never keep it in your wallet or purse.)
Take Advantage of Browser and OS Features:
If a full-on password manager feels like too much too soon, at least use the built-in tools you might already have. If you’re in Apple’s ecosystem, iCloud Keychain can auto-generate and store strong passwords across your devices.
It’s not as cross-platform as Bitwarden, but it’s user-friendly and much better than reusing weak passwords. Similarly, Google’s Password Manager (through Chrome/Android) can create strong passwords and even alert you to breaches.
These aren’t quite as feature-rich as standalone managers, but they’re a decent starting point if you feel hesitant about a new app.
Learn As You Go:
You don’t need to become a cybersecurity expert overnight. Even reading this guide is a great first step — go you! 🎉
Keep learning little things: what a phishing email looks like, how to turn on 2FA (usually under Security or Login settings). And when you hear about a breach in the news that affects a site you use, take that as a prompt to update your password there — and anywhere else similar.
Security is an ongoing process, but it really does get easier with habit. Before you know it, you’ll be the one giving advice.
For Seniors: “I Didn’t Grow Up With This Tech – Help!”
Seniors face some unique challenges with passwords. There may be memory issues, less familiarity with apps — and unfortunately, scammers often target older adults.
But the good news is, you can absolutely stay secure online. Here are some simple pointers tailored for seniors (and for family members helping them):
Use Password Managers with Simplicity in Mind:
Look for a password manager that emphasizes ease of use. Some seniors find built-in managers like iCloud Keychain (on Apple devices) simpler, since they’re integrated and don’t require learning an extra app.
Others might prefer a standalone app with a clean, clear interface. For example: RelyPass on iPhone was designed to feel straightforward — if you’re already comfortable with iPhone, RelyPass could feel like a natural fit.
It won’t bombard you with tech jargon — it just stores your logins securely. Also consider managers that offer family plans: 1Password Families, for instance, allows trusted family members to assist and even has an emergency access option.
Leverage Biometric Logins:
Many devices now let you log in with a fingerprint or facial recognition. For seniors, this is a huge convenience — no more typing complex passwords on tiny screens.
If you have a smartphone, set up fingerprint or FaceID unlocking. The same goes for your password manager app — this way, you only need to remember your master password occasionally, while your finger or face does the job securely day-to-day.
Write Down Password Hints (Securely):
If memory is a concern, a useful trick is writing hints for your passwords rather than the passwords themselves.
For example:
if your Facebook password is GeorgiaLake1975!, you might jot down a hint like “state + water + year + !”.
That way, if you forget, the hint jogs your memory — but wouldn’t help a stranger. Keep such a hint sheet locked away safely at home. The goal is to avoid getting completely locked out, while keeping info away from prying eyes.
Beware of Phone Scams and “Support” Calls:
Sadly, scammers often call seniors pretending to be from Microsoft, Amazon, or even government agencies. They’ll ask for passwords or remote access to your computer.
Rule of thumb: Never share passwords or verification codes with anyone who calls you — companies will never call you out of the blue and ask for login info. If you get such a call, hang up.
If you’re concerned it might have been legitimate, call the company back using their verified customer service number. Same goes for emails: If you get an alarming message saying “Your account is in danger, click here,”
it’s likely phishing.
When in doubt, ask a family member or friend you trust to help check.
Use Two-Factor Authentication — It’s Not Just for Kids:
2FA might sound complicated, but it can be as simple as receiving a text message with a code.
If you have a cell phone, you can use 2FA. It provides tremendous extra protection. For key accounts like email and banking, ask a family member to help set it up. Then even if you accidentally give away a password or use a weak one somewhere,
the second factor can still protect you.
Just be sure to keep track of backup codes or methods (you could even print them and store them with other important documents), especially if you ever get a new phone.
Password Journal — Pros and Cons:
Some seniors prefer an old-fashioned notebook for passwords. This can work — but only if you’re disciplined about security. Keep the notebook in a locked home safe or safety deposit box when not in use.
Don’t carry it around or leave it lying around the house. Writing passwords down isn’t ideal, but if it’s a choice between reusing one weak password everywhere (bad)
or having strong, unique passwords written in a locked book (better — but protect that book!), the latter still prevents digital theft.
Treat a password journal like you would your will or important financial papers —
lock it up. And consider it a temporary bridge while you transition to a password manager.
Ask for Help — It’s OK!:
Cybersecurity can feel intimidating at first. Don’t hesitate to ask a family member, friend, or even tech support from companies for help setting up a password manager or 2FA.
Many libraries and community centers even offer tech classes for seniors. A little guidance can go a long way. And remember: being secure online is a learning process for everyone — young and old alike.
For Teams (Families or Workplace Groups): “We Have to Keep Everyone Safe”
Whether you’re securing a family household or managing a team at work, the challenge is simple but tricky: you need multiple people on the same page.
One weak link can jeopardize the whole group — whether it’s someone sharing the Netflix password on a sketchy site or an employee using Company123 as their work email password.
Here’s how to promote good password hygiene in a group:
Use a Shared Password Manager Vault:
Many password managers offer family or team plans. These let you create a shared space for common passwords (like the Wi-Fi password, streaming logins for a family, or project accounts for a work team) while still keeping personal credentials private.
It’s way more secure than emailing passwords around. For families, something like 1Password Families or Dashlane Family makes it easy to manage important shared logins (like a joint bank account) safely.
For businesses, enterprise-focused managers (1Password Business, Dashlane Teams, Bitwarden Enterprise, etc.) let admins enforce strong passwords and 2FA for everyone — and onboard/offboard employees easily.
Enforce Strong Password Policies:
If you’re the admin or head of household, set some ground rules.
Example:
require that “everyone must use a password manager for work accounts and enable 2FA.” Encourage — or enforce — using unique passwords.
In a business, you could even configure systems to block reuse of old passwords
and enforce a strong minimum length (NIST says 8 characters minimum but 15+ is now recommended — pages.nist.gov).
Want to motivate people?
Here are some stats: “Folks, 81% of hacks are due to weak passwords (bnd.nd.gov).
We don’t want to be part of that statistic — let’s all do our part.”
Train and Phish Test (for Work Teams):
Regularly educate your team about phishing and social engineering. Run simulated phishing emails (there are services for this, or you can DIY) so people stay sharp. It’s better they fail a fake phishing test and learn than fall for a real one.
For families, it can be as simple as talking about scams going around: “Hey, I heard there’s a text scam saying ‘Netflix account locked.’ If you see that, ignore it.” Small conversations go a long way.
Plan for the Worst — Recovery:
Make sure there’s a way to recover accounts if someone leaves the team
or in case of an emergency.
In a family, ensure someone besides the primary account holder knows how to access critical accounts — maybe through an emergency access feature in the manager or by sealing info in an envelope for a trusted relative.
In a business, keep admin access or recovery keys stored securely so you’re not locked out if an IT person quits. This isn’t directly about passwords — but it’s absolutely about account resilience.
Avoid Shared Accounts When Possible:
It’s better for each user to have their own login with proper permissions than for multiple people to share one password. Shared logins often mean people share that password insecurely (“Just Slack me the login!”) — and accountability goes out the window.
Many services offer separate accounts or sub-accounts for users — use them. If you must share a login, share it securely via a password manager — not by email or text.
Regular Check-ins:
For a work team, periodically audit password habits. Are people really using the password manager? Any accounts still using default passwords?
For a family, consider an annual “security spring cleaning” chat: update key passwords, close old accounts you no longer use (fewer accounts = less risk), etc. Keeping security as a recurring conversation helps make it stick.
By implementing these practices, teams — whether it’s a couple managing finances or a company of 500 — can dramatically reduce the risk of a password-related breach.
It really is a group effort: your security culture matters just as much as the tools you use.
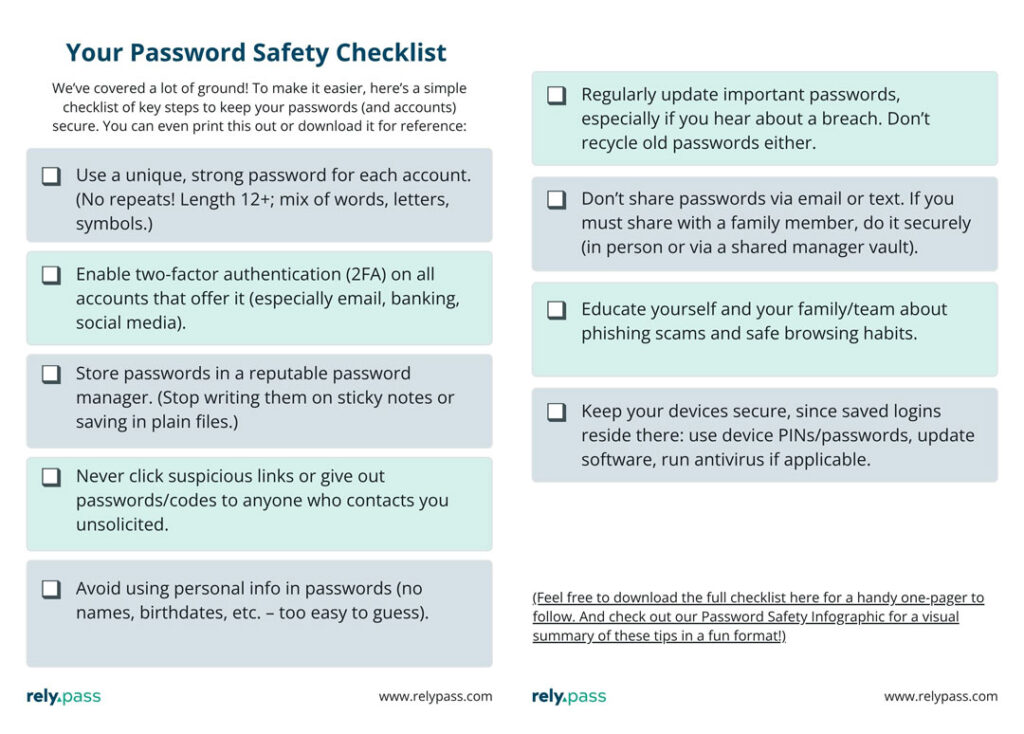
Your Password Safety Checklist & Infographic 📋
Conclusion: Take Control of Your Digital Security Today
Just by reading this guide, you’ve already taken the first step toward better security. 🏆
Now it’s time for action. The threat from weak passwords is real — but so is your power to prevent it.
By putting the tips above into practice, you’ll dramatically reduce your risk of getting hacked. And honestly, you’ll also enjoy something even more valuable: the peace of mind that comes from knowing your personal information is locked up tight.
Let’s quickly recap the emotional and practical payoff here:
- You’ll avoid the nightmare Lisa faced — no stranger rifling through your bank account or personal emails because you’ve fortified your passwords and added that crucial second lock (2FA) (elm.umaryland.edu).
- You’ll join the ranks of the cautious and savvy. Instead of thinking “It won’t happen to me,” you’ll know you’ve made it much less likely to happen to you.
- Managing passwords will stop being a source of anxiety. Imagine no longer needing to remember 50+ logins or stressing every time a new breach hits the news.
A bit of up-front effort now leads to long-term ease.
Don’t wait for a security scare to make changes. Start today.
Begin with just one account — maybe your email — and secure it with a strong new password and 2FA. Then move on to others, one by one.
If you need an easy win, try a free password manager like RelyPass or Bitwarden for a week
and see the difference for yourself.
And don’t keep this knowledge to yourself: share it with your family, friends, or coworkers.
You might save them from a future crisis.
Finally, remember, you’re not alone in this journey. We’re all learning how to navigate the digital world’s challenges together. Whenever you feel unsure, come back to this guide,
use the checklist, or check trusted resources like the FTC or NIST guidelines for extra reassurance (for example: NIST emphasizes using passphrases 15+ characters long —
“long and strong” is the new norm, Gadellnet.com).
You’ve got this.
Stay safe out there, and give yourself a pat on the back for taking password safety seriously.












Constant Password Reset Loop: What It Means and How to Fix It - RelyPas
July 31, 2025[…] How to Keep Passwords Safe (Ultimate Guide &… […]
Password Reset Email Not Arriving: Major Causes and Proper Solutions - RelyPas
July 31, 2025[…] sure sensitive information is safely protected while it’s being sent or […]
Autofill Not Working: Best Solutions to Solve This Issue - RelyPass
July 31, 2025[…] Learn more: How to Keep Passwords Safe […]
Why Is Safari Not Saving Passwords and How to Fix It - RelyPass
July 31, 2025[…] Learn more: How to Keep Passwords Safe […]
Facebook Login Issues? 12 Fixes for Error & Password Problems - RelyPass
July 31, 2025[…] Store login details safely. […]